The dark web’s two faces: Charity fundraisers alongside extortion and kidnapping
Internet criminals, responsible for 84% of global scams, uphold codes of conduct and an arbitration system to govern their society
The dark web harbors a wide range of sinister activities like murder for hire, weapons and illegal drugs for sale, distribution of child pornography, as well as robbery, kidnapping, extortion and infrastructure sabotage. It represents the most nefarious recesses of the internet. Yet even this criminal realm lives by a set of norms and rules. “They have their own code, although we must never forget that they are criminals,” said Sergey Shaykevich, director of Check Point Software’s Threat Group during CPX Vienna (Austria) cybersecurity summit. “84% of all scams happen online,” said Juan Salom Clotet, chief of Spain’s Cybersecurity Coordination Unit (Civil Guard). This same dark web organizes charity fundraisers, celebrates holidays, disciplines inappropriate behavior and has its own “judicial system.”
The well-known web we access daily through popular browsers represents just 5% of the internet. It’s just the surface of the deep web ocean of information that is intentionally hidden or not meant to be easily accessed. Kaspersky security researcher Marc Rivero said, “The deep web covers anything not picked up by regular search engines, like sites needing logins and private material. On the other hand, the dark web – a slice of the deep web – is all about using hidden networks to keep users and sites anonymous. It’s commonly associated with illegal activity.”
“The deep web serves both legitimate and questionable purposes,” said Rivero. “It includes secure communication platforms for sharing information, uncensored social networks and support groups. It grants access to restricted data like academic or government documents, specialized forums for knowledge exchange, and entertainment sources such as digital marketplaces, gambling sites and online gaming platforms.”
Living on the deepest ocean floor of the deep web is a small criminal network that, according to Telefónica Tech’s María Jesús Almanzor, launches “90 million cyber attacks worldwide, costing 10.5 billion euros [$11.5 billion]. If cybercrime were a country, it would rank as the world’s third largest economy, after the United States and China.” Shaykevich researches this part of the web using “isolated computers and technical precautions” to defend against the rampant malware there.
To access the deep and dark web, browsers like Tor, Subgraph, Waterfox and I2P are used. Tor (short for The Onion Router) functions by connecting randomly to an entry node, forming a circuit of encrypted intermediate nodes for secure data transmission. The traffic within the circuit remains anonymous, with the entry and exit points being the most vulnerable.
“Tor was not designed for crime,” said Avast’s Deepan Ghimiray, but criminals quickly recognized and leveraged its capabilities. Silk Road was one of the first. The dark web marketplace was created by Ross Ulbricht in 2011, and was shut down two years later by the FBI. Ulbricht, also known as Dread Pirate Roberts, is now serving a life sentence for money laundering, computer hijacking, and drug trafficking conspiracy.
“Accessing the dark web isn’t technically difficult – just download a specialized browser. But it’s risky. All sorts of malware, scams and more lurk there. Be cautious, protect yourself with security software, a firewall and a VPN for privacy,” warned Rivero.
Exams and interviews to become a criminal
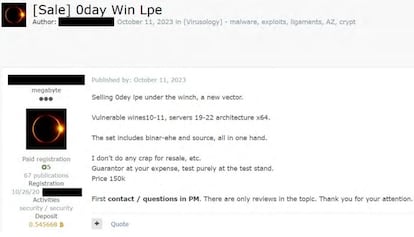
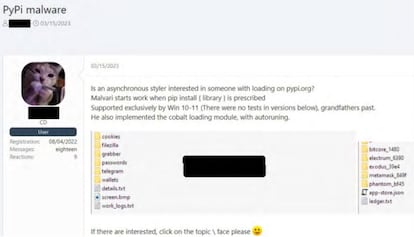
Shaykevich says that accessing the dark web’s sewers typically involves an “invitation from a criminal mafia member or undergoing an investigation by them.” Rivero elaborated: “Some forums are public, allowing anyone to register, while others are exclusive and involve a strict selection process. Usually, methods like invitations by existing members or administrators are used, relying on recommendations from within the community. Some forums may ask users to fill out an application or undergo an interview to assess their suitability. Others might require users to demonstrate knowledge on a specific topic through exams or test posts, or be recommended by reputable dark web users.”
Once you pass these tests, the underworld of the internet is surprisingly similar to the rest of the world. “They’ve got their own chats and even use these hidden Telegram channels to hire services or show off what they’ve done, putting the names of their victims out there,” said Rivero. He also described an arbitration system used to resolve user disputes, like the one that dismantled the LockBit extortion group after it failed to equitably distribute the ransom from a kidnapping. The dark web forums held a trial, heard an appeal and issued a final conviction. “After that, it was really tough for them to work again because they lost their credibility, which is key in the dark web.”
In the underworld, you can easily find data belonging to regular internet users (Google One will check if your accounts are compromised or available on the dark web). The web pages tend to be simple, since no marketing strategy or search engine optimization is needed. The dark web also has user forums and chat apps like the regular world.
Shaykevich remembers Conti, a kidnapping and extortion group that supposedly disbanded after a leak. They once had “200 people and physical offices in Moscow. We analyzed leaked chats ranging from notices about freshly painted doors, to warnings about discussing malware in the building’s cafeteria.”
“The dark world is not that different from the real world,” said Shaykevich. “They throw parties, go on vacations, and even raise money for orphanages. They’re just people – yes, criminals – but they’ve got kids and some think they’re moral people. Some ransomware crews absolutely refuse to hit hospitals, and also steer clear of ex-Soviet countries. But let’s not forget – they’re still criminals.”
Attacks on institutions like hospitals are considered highly reprehensible in a world where successful robberies and kidnappings are used as part of publicity strategies. “Being a hacker is like running a business without integrity. They kidnap and extort people. But the worst is when they target a hospital, because they can kill people. And it’s all for money,” said Check Point VP Francisco Criado.
Sign up for our weekly newsletter to get more English-language news coverage from EL PAÍS USA Edition
Tu suscripción se está usando en otro dispositivo
¿Quieres añadir otro usuario a tu suscripción?
Si continúas leyendo en este dispositivo, no se podrá leer en el otro.
FlechaTu suscripción se está usando en otro dispositivo y solo puedes acceder a EL PAÍS desde un dispositivo a la vez.
Si quieres compartir tu cuenta, cambia tu suscripción a la modalidad Premium, así podrás añadir otro usuario. Cada uno accederá con su propia cuenta de email, lo que os permitirá personalizar vuestra experiencia en EL PAÍS.
¿Tienes una suscripción de empresa? Accede aquí para contratar más cuentas.
En el caso de no saber quién está usando tu cuenta, te recomendamos cambiar tu contraseña aquí.
Si decides continuar compartiendo tu cuenta, este mensaje se mostrará en tu dispositivo y en el de la otra persona que está usando tu cuenta de forma indefinida, afectando a tu experiencia de lectura. Puedes consultar aquí los términos y condiciones de la suscripción digital.









































